In the 2026 threat landscape, the old “fortress” mentality—building high walls and hoping for the best—is obsolete. We live in the era of “Assumed Breach.” Companies now operate under the assumption that they are already compromised.
For a student, this means one thing: You cannot defend what you do not understand.
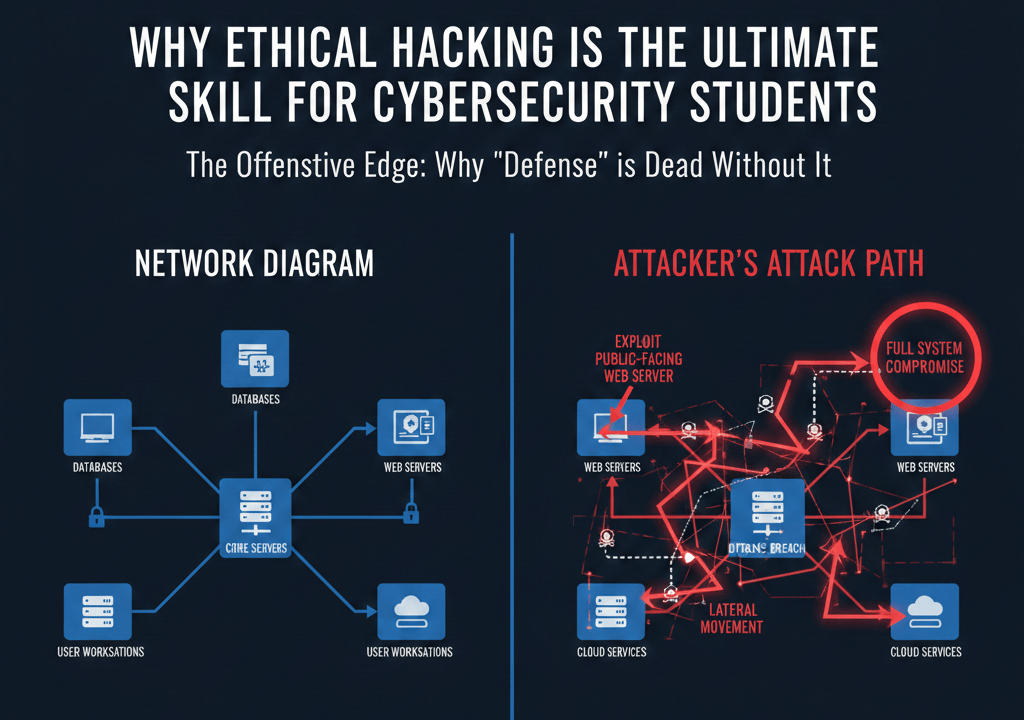
Defenders who study ethical hacking (Red Teaming) learn to think like the enemy. They don’t just see a firewall; they see a bypass. This “hacker intuition” is the most valuable asset you can bring to a job interview. It shifts your perspective from checking boxes to hunting threats.
Automated scanners are great at finding missing patches, but they are terrible at understanding context. This is where you come in.
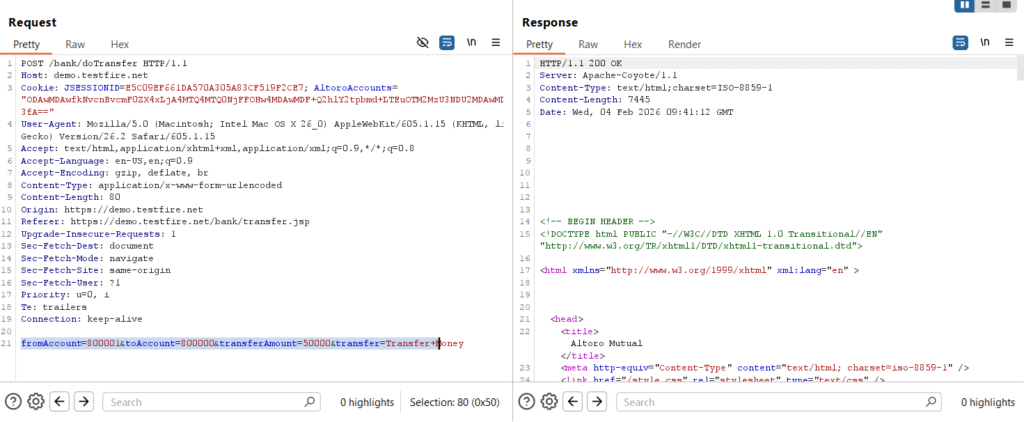
The most dangerous vulnerabilities in 2026 aren’t complex code injections; they are Business Logic Vulnerabilities. These are flaws where the app technically “works,” but the outcome is wrong.
Real-World Example: Consider the “Currency Conversion Hack.” A researcher intercepted a checkout request and changed the currency from USD to TRY (Turkish Lira). The system kept the number “1” but processed it as 1 Lira instead of 1 Dollar, resulting in a massive discount. Automated tools missed this because the math was “valid,” but the logic was broken.
Learning to spot these flaws requires human creativity—something AI still struggles to replicate.
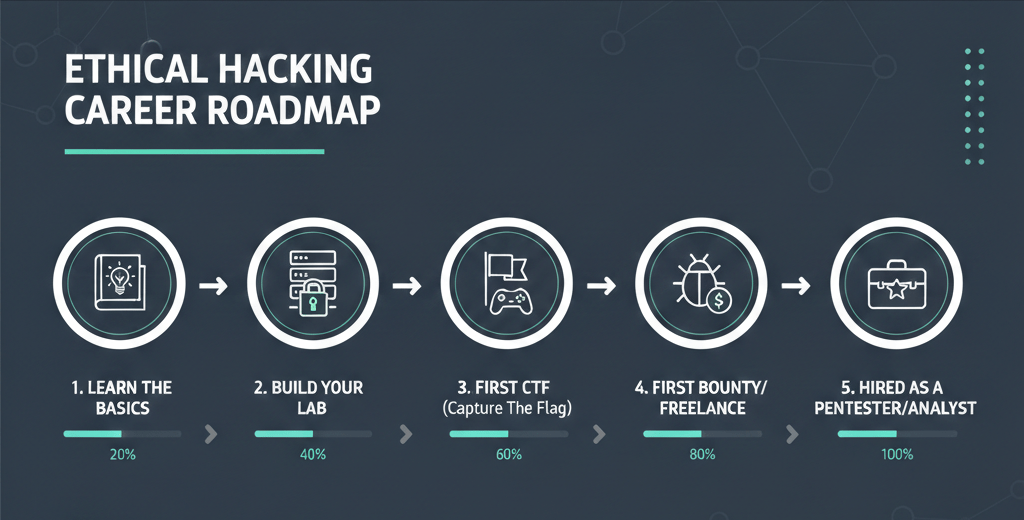
You don’t need to wait for a degree to start working. The Bug Bounty Economy has democratized experience.
Pro Tip: Employers in 2026 care less about your CGPA and more about your Portfolio.
Theory is useless without practice. To survive in cybersecurity, you need to build a Home Lab. You don’t need expensive gear—just a willingness to break things safely.
The 2026 Starter Kit:
The demand for ethical hackers is exploding, with cybersecurity job growth projected at 33% through the next decade. But the roles won’t go to the students who memorized tools. They will go to the ones who built labs, hunted bugs, and learned the art of offensive security.
Your move: Download Kali Linux, sign up for a CTF, and start breaking things to learn how to fix them.
–By Ayur Hansda

ASD Academy offers coding and cybersecurity programs with 1-to-1 online training, featuring expert-led video courses for all levels.